Multi-dimensional Approach Needed Against Cyber Threats..
Several recent high profile cybersecurity cases in Singapore have gripped the industry.
Such as Australia-based HR solutions provider, PageUp; Singapore largest healthcare service provider, SingHealth and non-profit organisation, Securities Investors Association of Singapore (SIAS).
Fresh in the minds of many here is probably SingHealth, which reported that 1.5 million records from its database have been illegally accessed.
This has created major ripples and resulted in government IT projects being put on hold while investigations are underway.
PageUp, a private entity which provides HR services such as talent recruitment and management, consulting and its HR software as a service (SaaS) app. Its recent breach is linked to the government as well.
Careers@Gov portal which is under Public Service Division (PSD) in the Prime Minister’s Office (PMO), handles jobs from the public agencies. This is also a global cybersecurity incident as PageUP is a global company with presence in over a 100 countries, and it happened shortly after EU’s GDPR came into effect.
Some industry observers however, pointed to concern to the cybersecurity incident reported by SIAS.
In cybersecurity, this is known as advanced persistent threat (APT) or zero-day, where a threat lays dormant after its penetration of computer systems. And during the time in stealth mode, the perpetrators help themselves to information right under the nose of systems’ owner.
If there are any apathy to be mindful of safety measures and cyber hygiene, these cases should remind individuals and organisations alike to be precautious.
Indifference tend to come from individuals and SMEs. It is not uncommon for both groups to adopt an “it won’t happen to me” mentality. Another is the thought that, “I am just a small outfit, no cyber criminals would target me”.
This is quite a dangerous form of mindset to adopt. Modus operandi for data exfiltration and system attacks have evolved.
Criminal syndicates are keeping abreast with technology and hacking techniques. With automation and robotics being weaponised and easily deployed, it is no longer ‘tedious’ for hackers to launch broad base attacks to steal data.
On the other hand, it is also humanly impractical for endusers to be vigilant. But all is not lost as individuals and SMEs can adopt simple habits and tap onto inexpensive tools to help strengthen their IT fortresses.
Below are some recommendations from our cybersecurity team to help users bring up their cyber hygiene quotient:
One of the most common threat vectors is email. Many cyber breaches occur due to users inadvertently (or not) clicking on hyperlinks. Some of these emails tap onto the curiosity of endusers, via file attachment with subject titles related to payment. Some are cleverly cloaked but many are not. Users are encouraged to pause for a moment, take a closer look at the links and assess their legitimacy. There are usually tell-tale signs that they are not. Such as email from an unknown entity, or badly worded messages
To counter cleverly disguised malicious threats in hyperlinks, users can hover their mouse cursor if they are using desktop or laptop computers. A floating message would appear with some indication to the origins of the hyperlinks, these are meta data and users can tie it back to the sender, the organisations where such emails come from or assess if the descriptions in the links are legit
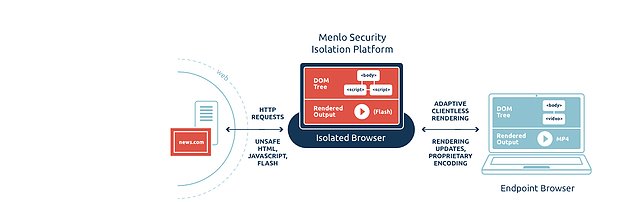
As it is humanly impossible to be on-guard indefinitely, tapping onto technologies is no longer an option. Besides the essentials like antivirus software, firewall protection, there is also the option to consider ‘isolation’ protection tactic. This is achieved by deploying an ‘in-between’ safety mechanism, where a malware successfully hit in the event that computer users accidentally click onto a malicious link. The malware would then entre the in-between system, usually another computer, which does not contain important information and is located in a different location





